Privacy Protocols Revive: Is the Old Era of Zcash and Monero Ending as a New Privacy Ecosystem Begins?
Introduction
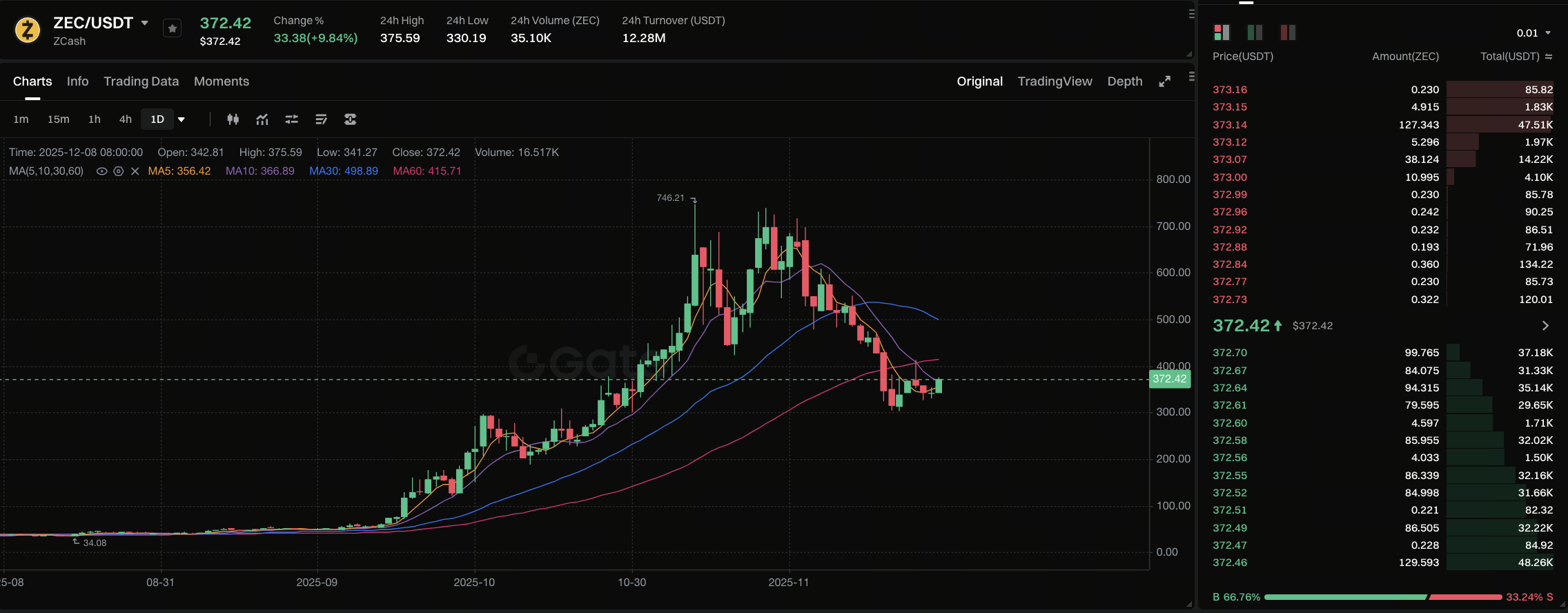
Source: https://www.gate.com/trade/ZEC_USDT
In fall 2025, privacy coins are back in the spotlight. Multiple market research and industry analyses indicate that legacy privacy coin Zcash (ZEC) has seen an explosive price surge: since September 2025, ZEC’s price has multiplied several times, reflecting renewed interest in on-chain privacy. Analysts believe that as global regulations strengthen KYC and similar measures, demand for blockchain anonymity is rising again. Maja Vujinovic, co-founder of Digital Assets Growth, noted, “Regulators are enforcing KYC strictly everywhere, so users who want privacy are returning to on-chain transactions.” In short, a combination of factors has driven the rise of privacy assets like ZEC, sparking discussion in the industry about a new cycle for privacy protocols.
The Previous Era of Privacy Coins: Zcash and Monero
Source: https://z.cash/
In the “old era” of privacy protocol development, Zcash and Monero stood out as the most representative projects. Zcash launched in 2016 and pioneered the use of zk-SNARK zero-knowledge proofs on blockchain, enabling encryption and concealment of transaction participants and amounts in shielded transactions. Early versions (Sprout/Sapling) introduced both transparent and shielded addresses, with later upgrades (such as the Orchard protocol) further enhancing privacy and scalability. Monero has provided default privacy for all transactions since 2014: its core technologies include stealth addresses, ring signatures, and RingCT confidential transactions, ensuring that sender, receiver, and amount details cannot be publicly traced on-chain. These mechanisms were widely popular during the 2017 crypto bull run and amid growing demand for anonymous payments.
However, the rise of privacy coins also brought stricter regulation. In 2018, Japan’s Financial Services Agency required domestic exchanges to delist privacy coins such as Monero and Zcash; in 2021, South Korea imposed a blanket ban on privacy coin support and trading services at exchange platforms. Reports from 2024 show over 60 instances of privacy coin delistings globally, with Monero being hit hardest. That same year, the EU Parliament passed the Markets in Crypto-Assets Regulation (MiCA), imposing strict limits on anonymous crypto assets that fail traceability and compliance requirements, raising compliance barriers for mainstream regulated platforms. Under regulatory pressure, liquidity and acceptance of privacy coins dropped sharply. For example, in 2025 data—even as ZEC rebounded recently—the overall market cap of privacy-related assets remains significantly lower than mainstream cryptocurrencies, representing a small fraction of the total crypto market and highlighting their limited presence in mainstream markets.
Next-Generation Privacy Protocols
Faced with the limitations of legacy privacy coins, next-generation privacy protocols are pursuing diverse technical approaches:

Source: https://aztec.network/
Aztec
A programmable privacy Layer 2 protocol on Ethereum that brands itself as the “privacy world computer,” offering optional privacy at both transaction and smart contract levels. On Aztec, every wallet is essentially a smart contract; users can choose which asset information is public or kept private. The Aztec team has developed the Noir privacy programming language and an efficient SNARK proof system for building private smart contracts. Officially, Aztec is currently in testnet phase and plans to launch multiple privacy bridges (connecting Arbitrum, Base, etc.) in the future to enable seamless privacy functionality for existing DeFi protocols.
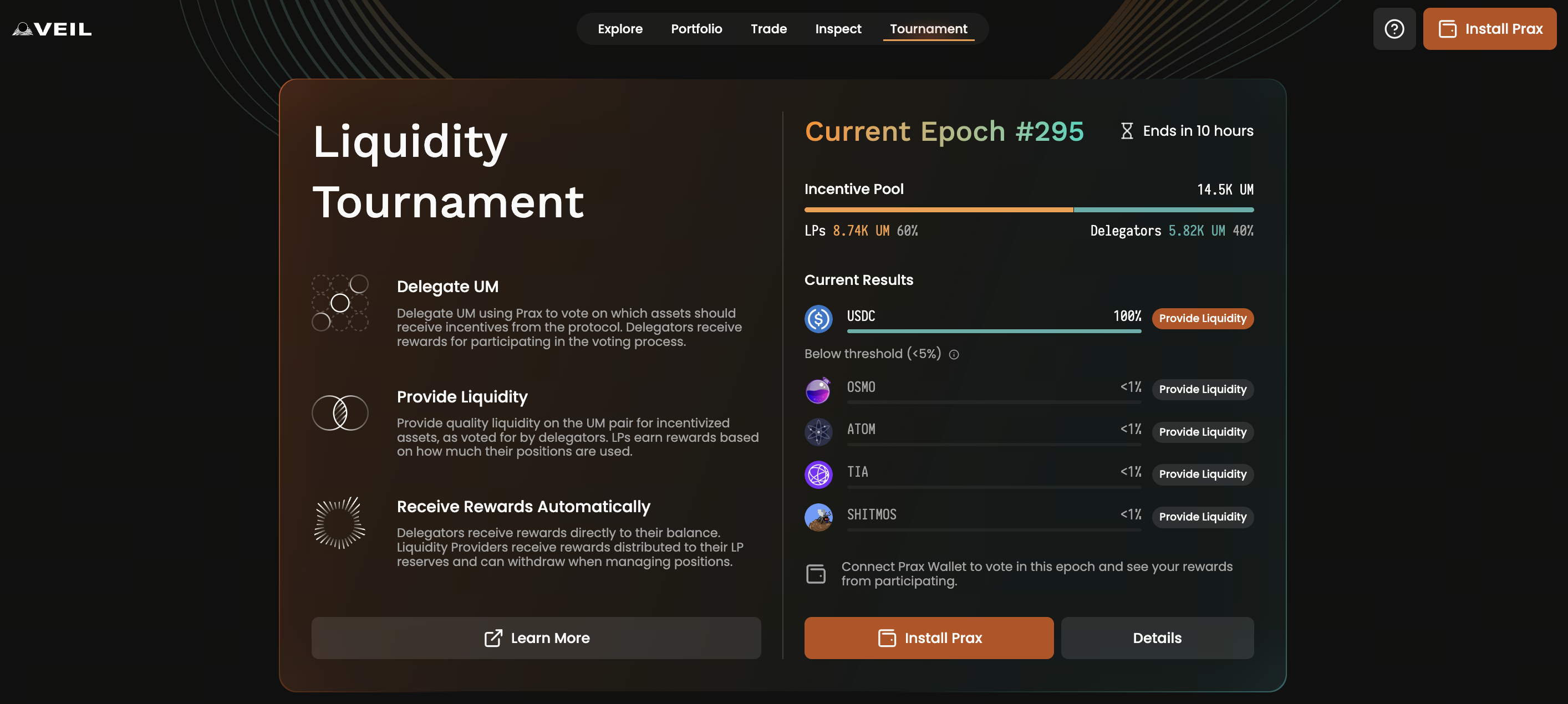
Source: https://dex.penumbra.zone/tournament
Penumbra
A cross-chain private PoS network and decentralized exchange built with Cosmos SDK. Penumbra records all value in a single multi-asset shielded pool and supports private transactions for any IBC-compatible asset. The system features built-in private staking and secret voting capabilities. On its testnet, Penumbra has achieved IBC cross-chain transfers (e.g., connecting with Osmosis testnet to map assets from other chains into its shielded pool), allowing any IBC asset to be traded privately within Penumbra. The protocol design means assets are automatically shielded upon entering Penumbra and revealed when withdrawn—delivering “chain-wide default privacy” with no transparent pools.

Source: https://www.zama.org/
Fully Homomorphic Encryption (FHE) Solutions
Projects like Zama are exploring fully homomorphic encryption to power privacy protocols. Zama has built a confidentiality layer that can plug into existing chains, enabling developers to execute smart contracts on encrypted data while preserving privacy using FHE and multi-party computation technologies. Its FHE virtual machine (FHEVM) lets Solidity contracts process encrypted inputs with decryption handled by a threshold node network. Research shows this “encrypted computation layer” can cover major chains like Ethereum and Solana without asset migration.
These new protocols generally emphasize composability and flexibility: they are often embedded in major public chain ecosystems (like Ethereum or Cosmos) and integrate with DeFi, DAOs, and other applications. Some solutions also address compliance needs: for instance, the Inco project likens itself to the blockchain world’s TLS/SSL layer, enabling law enforcement or regulators to access necessary information through programmable access controls; the “Privacy Pools” concept proposed by Vitalik Buterin and others uses zero-knowledge proofs to let users prove fund legitimacy while remaining anonymous—striking a balance between compliance and privacy.
Comparing New Protocols to Legacy Privacy Coins
In terms of composability, next-generation privacy protocols are mostly built on general-purpose smart contract platforms or cross-chain frameworks and natively compatible with DeFi and other applications. For example, Aztec and Nocturne deploy directly within the Ethereum ecosystem and connect to protocols like Uniswap or Yearn; Penumbra uses IBC to link into Cosmos for private cross-chain asset trading. In contrast, Zcash and Monero are relatively isolated: they mainly serve as payment tokens and cannot directly participate in mainstream on-chain finance ecosystems or provide programmable privacy.
For compliance, new protocols often incorporate auditable or selectively disclosable mechanisms. For instance, Vitalik’s Privacy Pools allow users to publish zero-knowledge proofs that satisfy regulatory requirements—demonstrating legitimate sources of funds without revealing full transaction histories; Inco supports programmable permissions so users can share their encrypted status with required auditors. This means new protocols leave room for compliance needs. Legacy privacy coins default to full anonymity with no built-in compliance options—a key reason they’ve been banned in many jurisdictions.
On functionality expansion, new privacy protocols offer richer scenarios and tools. Aztec supports building private smart contracts for use cases like confidential DAO voting or private lending; Penumbra is more than a private exchange—it also supports private staking and governance. By contrast, traditional privacy coins focus mainly on anonymous transfers with limited functionality.
In summary, next-generation privacy protocols outperform legacy coins in composability, compliance, and functionality through deep ecosystem integration, additional compliance mechanisms, and programmable privacy features.
Why Privacy Protocols Are Gaining Momentum in 2025
Privacy protocols have new momentum in 2025 due to several converging external factors. First, regulatory changes are driving markets to seek compliant privacy solutions. While many countries crack down hard on privacy coins, technical solutions that balance compliance—like Privacy Pools—are emerging. Industry statistics show demand for private transactions is growing: multiple market studies reveal that privacy-related trades account for a rising share of total crypto activity, indicating users’ need for transactional confidentiality is strengthening—not just short-term speculation.
Second, advances in AI and on-chain analytics are raising the bar for privacy protection. The Aztec team points out that as AI and on-chain surveillance tools (like Chainalysis or TRM) grow more powerful, ordinary addresses could soon be linked to real identities—making robust privacy safeguards essential. For example, big data analytics and machine learning algorithms can reveal transaction patterns and identity connections, prompting institutions and individuals alike to prioritize transaction secrecy.
Additionally, real-world demand is increasing. As assets migrate on-chain and institutions enter the space, their need for privacy grows: an Aztec co-founder admitted that while designing enterprise bond issuance on-chain, “potential users wouldn’t transact at all without privacy protection.” Clearly, large financial assets and traditional enterprises require substantial privacy guarantees to move business onto blockchain networks. Similarly, payment use cases—like digital currency transfers or stablecoin swaps—require both users’ and institutions’ transactional data to be appropriately protected.
Taken together, these drivers are ushering in a new cycle of value reassessment for privacy protocols in 2025: regulatory compliance needs spur innovation; AI heightens the call for privacy; real-world assets and payment scenarios create tangible use cases for privacy tech.
Core Project Analysis

Below are highlights of several leading privacy protocol projects and their recent progress:
- Aztec: A privacy-focused Layer 2 network built on Ethereum. Aztec has developed the Noir programming language and an efficient SNARK proof system for creating smart contracts with both public and private states. Previously released products include zk.money (Aztec v1) for private payments and Aztec Connect for private DeFi interactions. Notably, Aztec’s mainnet officially launched in November 2025—becoming Ethereum’s first fully decentralized privacy L2—with over 500 validator nodes participating at launch. The community is now focused on building multichain bridges and expanding the ecosystem to drive adoption of private transactions and smart contracts.
- Penumbra: A cross-chain private network and DEX within Cosmos ecosystem. Penumbra’s mainnet went live in July 2024. During testnet development, its biggest breakthrough was IBC cross-chain private trading: users could transfer assets from other chains via standard ICS-20 cross-chain transactions into Penumbra’s shielded pool automatically. The team plans to add Private ICA accounts soon so users can trade secretly on other chains before returning assets to the shielded pool. Overall, Penumbra has completed its multi-asset shielded pool and private DEX infrastructure; next steps focus on expanding ecosystem connections and developing more private use cases.
- Inco: Positioned as the confidentiality layer for blockchains—akin to TLS/SSL for the internet. Inco aims to provide confidential state management and programmable access controls for existing chains like Ethereum. In its architecture, Inco Lightning uses trusted execution environments (TEE) for near-native-speed confidential computing; Inco Atlas leverages FHE plus multi-party computation for stronger privacy guarantees. Official sources confirm Inco is currently running on Base testnet (Sepolia) with plans to support more networks soon. Inco emphasizes seamless integration with existing developer tools so devs can write private Solidity smart contracts without needing cryptography expertise.
- Zama: An FHE-based privacy layer protocol. Zama has built a fully homomorphic encryption blockchain protocol enabling smart contract execution on encrypted data. Developers can write contracts in Solidity or other languages using Zama’s encrypted data types and operations to process encrypted inputs on-chain. All encrypted computations occur off-chain with verification; data is only decrypted via threshold nodes when authorized. Zama has released multiple FHEVM testnet versions and plans mainnet deployment by December 2025. The project roadmap shows testnet v0.9 live now; v0.10 is in preparation; mainnet node deployment is scheduled.
- Privacy Pools: A protocol concept proposed by 0xBow (Ameen Soleimani) and others. Unlike typical mixing tools, Privacy Pools allow users to deposit funds into a shared pool then prove via zero-knowledge proofs that their funds didn’t originate from known illicit sources—without revealing their entire transaction history. Vitalik Buterin et al have discussed this approach in academic papers as a practical balance between compliance needs and privacy protection. Privacy Pools currently exist mainly as academic/design concepts but offer a blueprint for future compliant privacy tools.
Conclusion
The field of privacy protocols is at a critical transition point between old and new paradigms. Looking ahead, we can expect deeper integration between advanced privacy technologies and mainstream blockchain ecosystems—delivering confidentiality for decentralized finance (DeFi), RWA assets, and payment use cases. To meet regulatory compliance requirements, new privacy tools may need selective disclosure or auditability features built-in. The challenge lies in improving performance and usability without sacrificing decentralization or privacy guarantees. Technically, reducing computation costs for zero-knowledge proofs and FHE, optimizing dedicated hardware, ensuring protocol security, and enhancing user experience remain long-term challenges to overcome.
Overall, privacy is no longer optional—it has become fundamental infrastructure for blockchain development. As industry leaders say: “Privacy isn’t a niche feature anymore—it’s a prerequisite for serious applications.” The future of privacy protocols depends on continued technical innovation alongside evolving regulatory frameworks—to realize true “programmable privacy” and widespread adoption.
Related Articles

The Future of Cross-Chain Bridges: Full-Chain Interoperability Becomes Inevitable, Liquidity Bridges Will Decline

Solana Need L2s And Appchains?

Sui: How are users leveraging its speed, security, & scalability?

Navigating the Zero Knowledge Landscape

What is Tronscan and How Can You Use it in 2025?


