DePIN Identity Network and Real World Applications: How Humanity Protocol Brings on-chain Identity Into the Physical World
Humanity Protocol is a decentralized identity protocol designed to address fake identities and bot activity in Web3. Through Proof of Humanity combined with a biometric engine, users can prove that they are real and unique humans without revealing personal privacy. The system integrates zero knowledge verification, self sovereign identity, and an EVM compatible ZK Rollup architecture, and extends identity verification into real world environments through DePIN based physical infrastructure, forming an identity network that is usable across chains and applicable to physical scenarios.
As DePIN and multichain applications continue to develop rapidly, the absence of a trusted identity layer has become a central bottleneck. Resource allocation imbalance, infiltration of nodes by fake identities, and declining governance fairness all stem from this gap. Humanity Protocol addresses this by first verifying human uniqueness and then verifying identity only when required. This layered design preserves privacy and decentralization while establishing a verifiable human trust foundation. Identity no longer depends on centralized KYC systems, yet can circulate securely between physical devices, real world services, and on-chain applications, becoming a key technical pillar that allows DePIN ecosystems to scale.
This article explains what Humanity Protocol is and how it positions identity in the DePIN era. It analyzes the core mechanisms of Proof of Humanity, how biometrics and zero knowledge privacy architecture function, and how these components resolve identity challenges in decentralized physical networks. It also compares Humanity Protocol with other identity solutions, and outlines its real world applications and future direction across physical scenarios, RWAs, DAO governance, and Web3 infrastructure.
Humanity Protocol: The Identity Guardian of the DePIN Era

(Source: Humanityprot)
Humanity Protocol is a decentralized identity protocol focused on solving fake identity and bot problems in Web3. Through Proof of Humanity (POH) and a biometric engine, users can prove that they are real and unique humans while preserving privacy. By combining ZK Rollups, zero knowledge verification, and a DePIN architecture, Humanity Protocol not only establishes a trusted on-chain identity layer, but also extends identity verification into real world environments, becoming key infrastructure that connects multichain applications with physical services.
From Biometrics to Privacy Protection: Humanity Protocol Core Mechanisms
The core mechanism of Humanity Protocol is Proof of Humanity. Its defining feature is the separation of identity verification into two layers. The first stage confirms that a user is an independent and unique human. The second stage verifies whether the user corresponds to a claimed identity.
Unlike traditional KYC systems that build complete personal profiles, Proof of Humanity focuses on human uniqueness itself and follows a minimum necessary verification principle. The system combines biometric verification, zero knowledge proofs, self sovereign identity, and decentralized storage technologies. It runs on an EVM compatible Layer 2 ZK Rollup and provides identity verification services that can be reused across chains.
Why DePIN Network Expansion Depends on Proof of Humanity
The core value of DePIN lies in connecting real world resources with on-chain systems. However, without a trusted identity mechanism, these networks are highly vulnerable to fake nodes and automated scripts, which can distort resource allocation and undermine system reliability.
Proof of Humanity verifies that participants are real and unique humans without sacrificing privacy. This establishes a foundational trust layer for DePIN networks, ensuring that interactions between hardware nodes, service providers, and users are backed by verifiable human identity. As a result, decentralized physical infrastructure can maintain fairness and security as it scales.
How Humanity Protocol Solves Core DePIN Pain Points
For DePIN networks to achieve large scale adoption, the primary challenge is not hardware deployment, but the absence of an identity verification mechanism that is both trustworthy and privacy preserving. Without such a system, node authenticity is difficult to guarantee and resource allocation can be manipulated by fake identities.
Humanity Protocol addresses this challenge through Proof of Humanity. Rather than asking who you are, it focuses on whether you are a real and uniquely existing human. This approach establishes a decentralized human trust layer for DePIN at a foundational level. By combining AI driven palmprint and palm vein biometrics, zero knowledge proofs, self sovereign identity, and decentralized storage, Proof of Humanity enables high accuracy identity verification without exposing personal data. Running on an EVM compatible ZK Rollup, it provides a universal identity service for multichain decentralized applications.
When combined with DePIN networks composed of specialized hardware nodes, Humanity Protocol extends on-chain identity into physical infrastructure. This enables trusted verification across access control systems, hotel check in processes, and physical device login, addressing DePIN challenges related to authenticity, security, and scalability.
Humanity Protocol Deployment Path Within DePIN Identity Networks
In recent years, decentralized identity has expanded rapidly across NFTs, DAOs, and on-chain communities. However, most implementations remain confined to purely on-chain contexts, with limited connection to the physical world. If identity cannot move beyond the blockchain, it cannot function as true infrastructure.
Humanity Protocol uses a DePIN architecture to extend identity verification into decentralized networks of hardware nodes. Each node can perform biometric verification, generate on-chain identity credentials, and synchronize results through a ZK Rollup. Unlike traditional identity systems controlled by a single authority, these nodes are operated by distributed participants and sustained through token incentives. This structure provides the first practical path for on-chain identity to connect directly with real world environments.
DePIN Use Cases Enabled by Humanity Protocol
At the application layer, Humanity Protocol uses a dual verification structure composed of zkProofer nodes and Identity Validators to provide privacy preserving yet verifiable identity trust for real world scenarios. This allows on-chain identity to be used directly in physical environments such as building access control, secure passage systems, contactless hotel check in, public service verification, and event access. Users can complete verification using their Proof of Humanity identity without carrying physical documents.
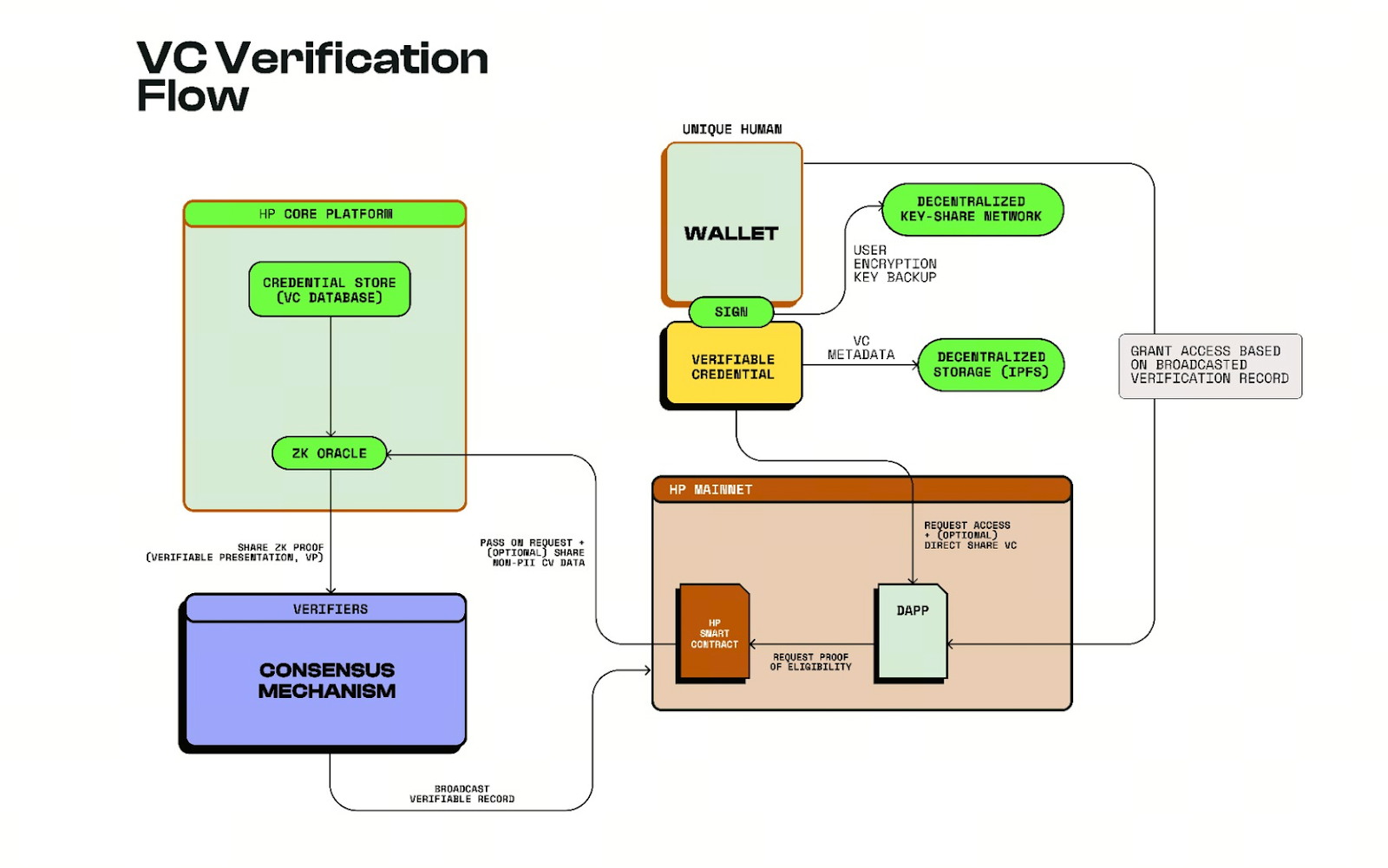
(Source: humanity-protocol.gitbook)
At the same time, the $H token serves as the economic core of the DePIN identity network. It is used to pay verification fees, reward node operators, and participate in governance, while also controlling access to identity credentials. With a fixed supply and non inflationary design, token value is closely tied to real usage demand. Institutional investors, including Hex Trust, have backed Humanity Protocol based on its ability to provide decentralized identity trust infrastructure applicable across RWA compliance, DeFi identity verification, and DAO Sybil resistance.
Humanity Protocol vs Worldcoin: Which Is Better Suited for DePIN Ecosystems?
From a DePIN perspective, the key difference between Humanity Protocol and Worldcoin is not who can prove you are human, but which system can be embedded into physical infrastructure networks. Worldcoin relies on highly centralized hardware devices for iris scanning. While efficient, device deployment, operation, and data governance remain tightly controlled by the organization, making it difficult to form an open node network.
Humanity Protocol, by contrast, is built on decentralized hardware nodes and zero knowledge verification. It emphasizes node replicability and network scalability, allowing identity verification itself to become participatory, incentivized, and governable infrastructure. This model aligns more closely with DePIN requirements for open networks, physical nodes, and economic incentives.
Future Outlook: Humanity Protocol as the Trust Layer of DePIN Infrastructure
From a long term perspective, Humanity Protocol’s value extends beyond solving on-chain identity issues. It aims to build a verifiable and scalable trust infrastructure for the entire DePIN ecosystem. As real world devices continue to move on-chain, demand for real identity, Sybil resistance, and compliance verification will only increase. Through decentralized hardware nodes, zero knowledge proofs, and token incentives, Humanity Protocol embeds Proof of Humanity into the underlying logic of physical networks. Identity becomes a core trust layer that supports resource allocation, permission management, and value flow, enabling DePIN to evolve from technical networks into scalable real world infrastructure.
Summary
When on-chain identity enters the physical world, it becomes more than a digital credential. Through DePIN, zero knowledge verification, and token incentives, Humanity Protocol is building an identity network that connects blockchain systems with real society, providing a verifiable human layer for future RWAs, physical services, and Web3 applications.
Related Articles

What is Fartcoin? All You Need to Know About FARTCOIN

Gold Price Forecast for the Next Five Years: 2026–2030 Trend Outlook and Investment Implications, Could It Reach $6,000?

Crypto Future Profit Calculator: How to Calculate Your Potential Gains

2026 Silver Price Forecast: Bull Market Continuation or High-Level Pullback? In-Depth Analysis of Silver Candlestick Chart

Crypto Futures Calculator: Easily Estimate Your Profits & Risks


