What is Humanity Protocol? Building a Human Identity Layer for Web3
Humanity Protocol is a decentralized identity verification network with strong Sybil resistance. It is designed to build a verifiable human layer for blockchain ecosystems. Through a Proof of Humanity mechanism and biometric technologies, the system can confirm user uniqueness and authenticity without exposing personal privacy. By integrating zero knowledge proofs, self sovereign identity frameworks, and decentralized storage architecture, it aims to become a key piece of infrastructure that connects real world identity and the on-chain world.
As Web3 applications expand, bot accounts and fake identities have become major obstacles for governance, airdrop distribution, and the functioning of on chain economies. Humanity Protocol addresses this through a layered verification architecture that includes a ZK Rollup, zkProofer, and Identity Validators, alongside a biometric engine that combines AI and hardware. This approach aims to deliver identity verification that balances privacy, security, and scalability. At the same time, DePIN extends identity verification into off chain settings, supporting a trusted human identity foundation for DAO governance, cross chain applications, and real world services.
This article explains what Humanity Protocol is, how its Proof of Humanity mechanism works, and how its core technical architecture is built. It also examines how biometrics, zero knowledge verification, and a DePIN identity network form a complete identity infrastructure, explains the $H token economic model and real world use cases, and explores the role Humanity Protocol may play in Web3 governance, airdrop mechanisms, multichain identity, and real world integration, helping readers understand its positioning and potential value in decentralized identity.
What is Humanity Protocol?

(Source: Humanityprot)
Humanity Protocol is a decentralized, Sybil resistant identity verification network. It aims to protect personal data privacy while bringing real humans into the on chain economy, positioning itself as a key bridge between real world identity and blockchain ecosystems.
Its core goal is to establish a trusted human layer in blockchain environments, allowing systems to distinguish real users from automated programs, and complete identity verification without sacrificing privacy.
How Humanity Protocol Works
Humanity Protocol’s core mechanism is called Proof of Humanity, or PoH. Compared with traditional identity verification, its key difference is that it operates on two levels.
First stage: Confirm that you are an independent and unique human.
Second stage: Verify that you are the person you claim to be.
PoH does not build a full personal profile. Instead, it focuses on human uniqueness itself, applying a minimum necessary principle, so identity verification stays as lightweight as possible.
The system combines multiple technical modules, including:
- Palmprint and palm vein biometrics
- Decentralized data storage
- Zero knowledge proofs
- Self sovereign identity frameworks
- Integration with real world KYC technologies
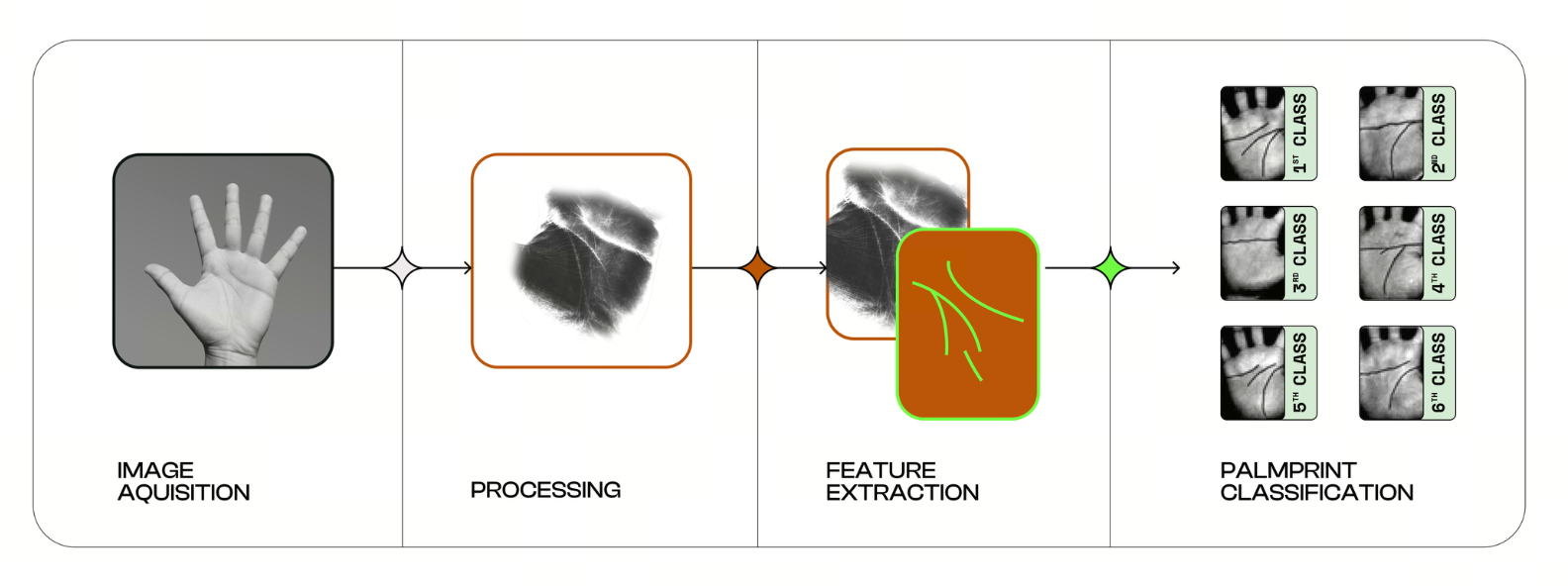
(Source: humanity-protocol.gitbook)
All processes run on an EVM compatible Layer 2 ZK Rollup, and the system can provide cross chain identity verification services to external networks.
Humanity’s Biometric Engine
A major technical highlight of Humanity Protocol is its combination of AI models and physical hardware to build a high trust human recognition system. Its palmprint and palm vein algorithms are trained on more than 500,000 biometric data samples, collected through specialized hardware devices that operate under visible light and infrared conditions.
This design brings several important advantages. On the privacy side, it uses a non intrusive approach that does not require facial scanning or fingerprint collection, significantly reducing user discomfort and perceived privacy risk. At the same time, biometric traits are inherently unique and difficult to replicate, making the system extremely hard to forge or impersonate.
From a practical perspective, this approach is low cost and highly scalable, supporting rapid deployment at large scale across diverse global use cases. The result is a human identity verification module that aims for high accuracy, strong reliability, and a very low barrier to use.
DePIN Architecture: Taking Identity Verification Beyond On Chain Systems
Humanity Protocol is not confined to blockchain environments. Through DePIN, it extends identity systems into real world scenarios.
These DePIN networks are composed of hardware nodes and can support a wide range of physical settings, including:
- Building access control and secure entry
- Contactless hotel check in
- Identity verification for physical facilities
- Login for on site events or public services
This makes Humanity Protocol one of the few Web3 identity infrastructures that aims to connect both on chain identity and the off chain world.
Three Core Technical Architecture Components of Humanity Protocol
- Self Sovereign Identity
After completing PoH verification, users receive a unique on chain identity that can be used for:
- DAO voting
- Airdrop eligibility verification
- KYC verification
- Credential based access permissions
All data is controlled by the user and does not depend on any centralized platform.
- zkProofer and Identity Validators
The network is composed of two types of nodes.
- zkProofer nodes generate zero knowledge verification proofs
- Identity Validators stake assets to participate in consensus and ensure verification results remain trustworthy
This layered structure is designed to balance transparency, security, and scalability.
- Zero Knowledge Privacy Protection
All biometric data is not stored as images. It is converted into encrypted mathematical representations. Even if the data is leaked, it cannot be reconstructed into personal information.
Humanity Protocol Tokenomics
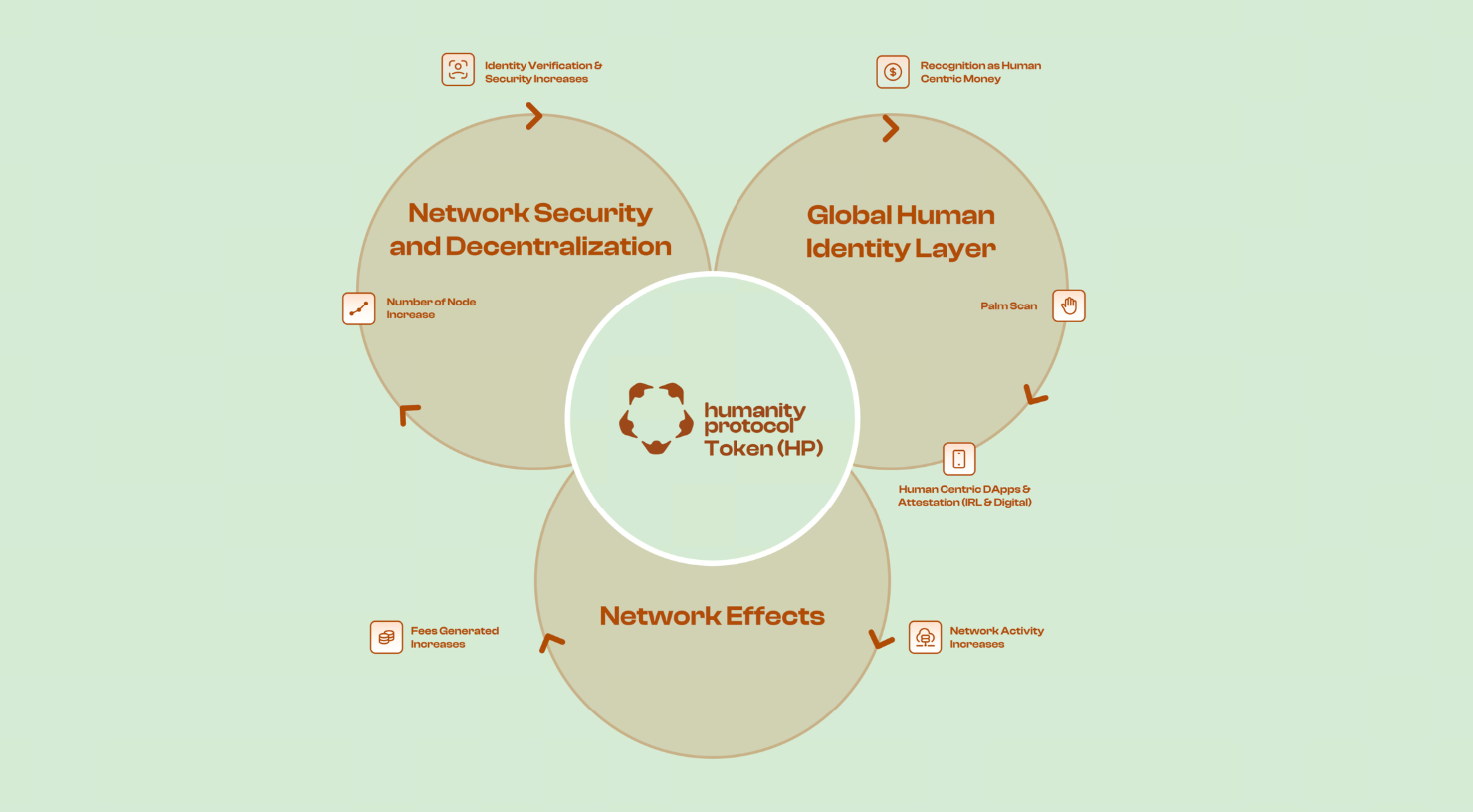
(Source: humanity-protocol.gitbook)
Humanity Protocol uses $H as its core economic unit, with a fixed total supply of 10 billion tokens. Based on the tokenomics model released by the project, the allocation ratios below summarize how $H is distributed, along with the functional positioning of each category within the ecosystem.
$H Token Allocation
The $H token allocation is as follows:
| Category | Percentage | Token amount |
|---|---|---|
| Ecosystem Fund | 24% | 2,400,000,000 |
| Identity Verification Rewards | 18% | 1,800,000,000 |
| Team and Early Contributors | 19% | 1,900,000,000 |
| Community Incentives | 12% | 1,200,000,000 |
| Foundation Operations Treasury | 12% | 1,200,000,000 |
| Investors | 10% | 1,000,000,000 |
| Human Institute Strategic Reserve | 5% | 500,000,000 |
The overall design emphasizes that rewards come from real participation, rather than keeping the system running through inflationary token issuance alone.
$H Token Utility
The main uses of $H include:
- Paying identity verification fees
- Node staking and verification rewards
- DAO governance voting
- Airdrops and community incentives
- Fees for credential based access permissions
Recent Developments in Humanity Protocol

(Source: Humanityprot)
Digital asset custodian Hex Trust has made a strategic investment in Humanity Protocol, highlighting strong institutional attention toward decentralized identity layers.
Hex Trust believes that the future development of DeFi, RWAs, and on chain governance must be built on:
- Verifiable real identities
- Strong Sybil resistance
- Privacy and compliance together
Humanity Protocol is positioned as one of the key infrastructures designed to address this structural challenge.
Future Outlook and Use Cases
The identity verification infrastructure built by Humanity Protocol may become a key foundational module in future Web3 ecosystems, providing verifiable human identity support for a wide range of decentralized applications. In governance, PoH can be incorporated into DAO decision processes to enable true one person one vote logic, preventing voting power from being manipulated by capital concentration or bots, and improving fairness and trust in decentralized governance. In incentive distribution, PoH can reduce Sybil attacks and bot farming, helping airdrop resources reach real and active participants more accurately. For off chain applications, when combined with DePIN identity devices, users can extend their on chain identity into real world settings, enabling contactless services such as hotel self check in, building access control, and membership verification.
PoH also has the potential to become a multichain identity pass, allowing users to move across different chains and applications with a single verifiable identity. As Layer 3 architectures and cross chain applications mature, Humanity Protocol may become a standard recognition layer for human authenticity in on chain environments, redefining the boundaries of trust and identity logic in Web3 from an infrastructure perspective.
Summary
Humanity Protocol is not simply building an identity verification product. It is attempting to create a layer of human authenticity infrastructure for decentralized networks. By integrating biometrics, zero knowledge proofs, DePIN, and self sovereign identity frameworks, it seeks to redefine where trust comes from in the Web3 world.
FAQ
How is Humanity Protocol different from traditional KYC or Web2 identity verification?
Humanity Protocol does not build a centralized personal data database. Instead, it uses Proof of Humanity to verify that you are a unique human, and relies on zero knowledge proofs to protect privacy. Users control their own identity data. Platforms cannot access complete personal information, while trusted verification can still be completed.Why does Humanity Protocol use biometrics, and does it create privacy risks?
Humanity uses palmprints and palm veins for identification. Data is not stored as images. It is converted into encrypted mathematical representations and verified with zero knowledge techniques. Even if the data is leaked, it cannot be reconstructed into real biometric traits, which significantly reduces privacy risk.What practical use does the $H token have for everyday users?
$H can be used to pay identity verification fees, participate in DAO governance voting, and function as part of node staking and reward mechanisms. For everyday users, $H is not only an investment asset. It is also a functional token that supports access to the Humanity identity ecosystem and participation in verification and governance.
Related Articles

What is Fartcoin? All You Need to Know About FARTCOIN

Gold Price Forecast for the Next Five Years: 2026–2030 Trend Outlook and Investment Implications, Could It Reach $6,000?

Crypto Future Profit Calculator: How to Calculate Your Potential Gains

2026 Silver Price Forecast: Bull Market Continuation or High-Level Pullback? In-Depth Analysis of Silver Candlestick Chart

Crypto Futures Calculator: Easily Estimate Your Profits & Risks


