Global Ledger: Cryptocurrency money laundering takes only 2 seconds, hackers move 76% of illicit funds before disclosure
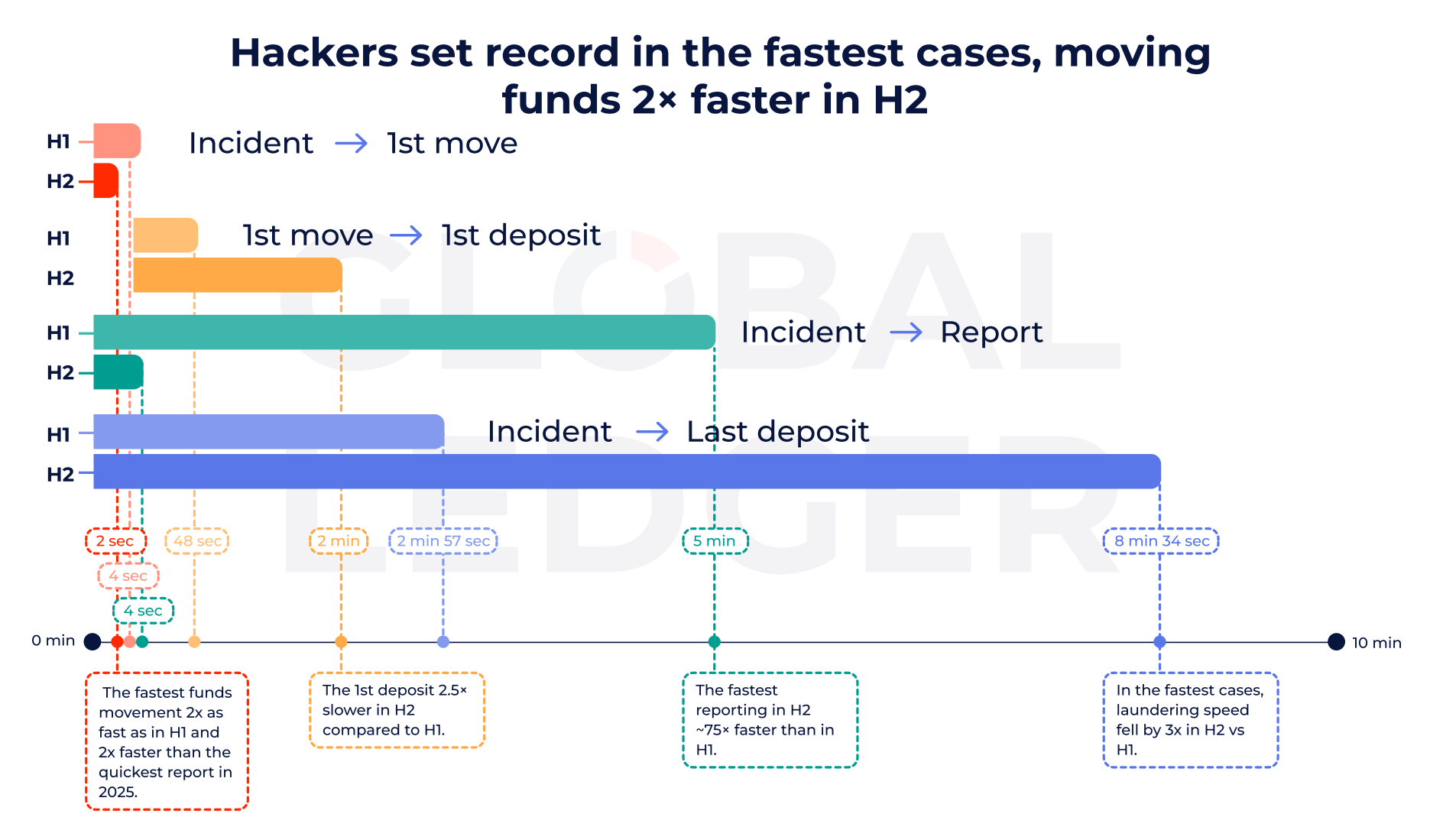
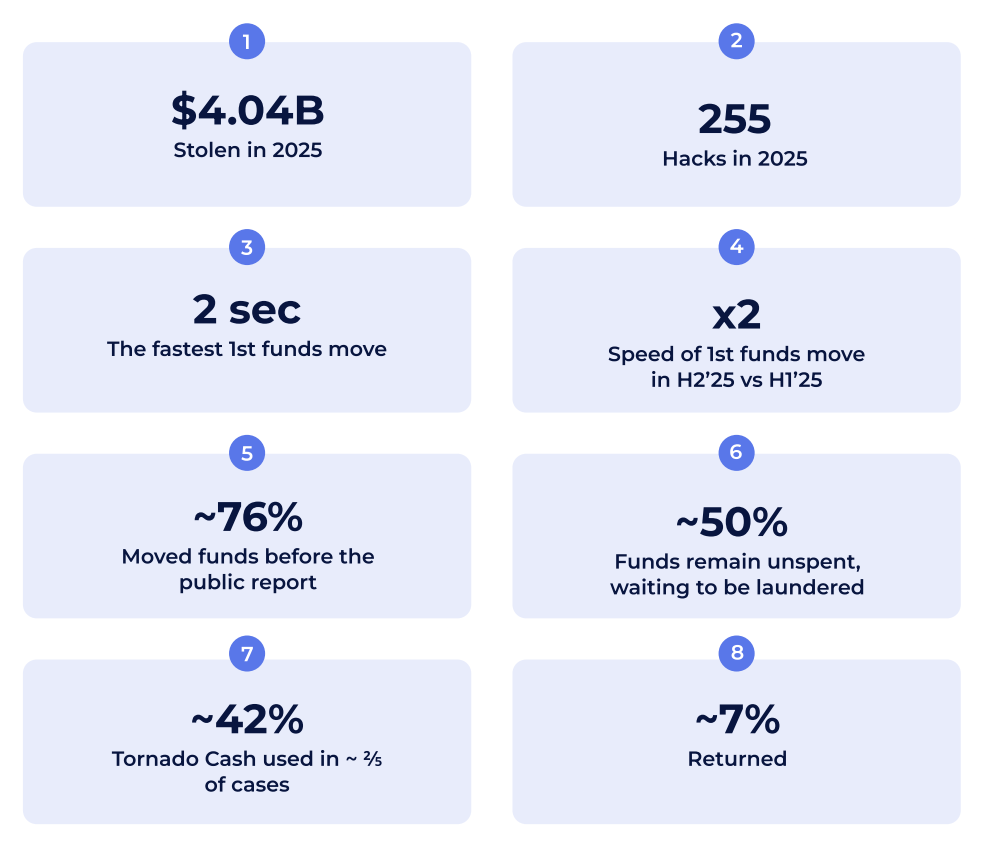
Cryptocurrency hackers can now transfer stolen funds within as little as 2 seconds after an attack begins, often moving assets before victims disclose data leaks. Global Ledger’s analysis of 255 crypto hacking incidents in 2025 draws a clear conclusion: 76% of funds are transferred before public disclosure, and this rate increased to 84.6% in the second half of the year.
The Speed Revolution: 76% of Stolen Funds Transferred Before Disclosure
(Source: Global Ledger)
This speed is shocking. According to Global Ledger, in 76% of hacking incidents, funds are moved before the attack is publicly revealed, rising to 84.6% in the latter half of the year. This means attackers often act before exchanges, analysis firms, or law enforcement can coordinate a response.
This “pre-disclosure” tactic is highly sophisticated. When a hack is not yet public, the addresses involved are not flagged, and exchanges or blockchain analysis firms are unaware these addresses hold illicit funds. Transferring funds at this stage can proceed smoothly, without triggering alerts or freezes. Once the incident is disclosed, these addresses are quickly blacklisted, making subsequent transfers much more difficult.
The increase from 76% in the first half to 84.6% in the second half of 2025 indicates hackers are getting faster. This evolution may be driven by automated scripts (triggering transfer commands immediately after a successful breach), precise timing calculations for victim responses, and the maturity of cross-chain bridges and tools that facilitate quick transfers. For victims, this speed means the window between “discovery of theft” and “funds moved” is nearly zero, leaving little chance to freeze assets.
However, speed only explains part of the problem. While initial transfers are now nearly instantaneous, the full money laundering process takes longer. In the second half of 2025, hackers typically take about 10.6 days to reach final deposit points like exchanges or mixers, up from around 8 days earlier in the year. In short, the initial theft is a sprint, but laundering is a marathon.
Two-Stage Timeline of Crypto Money Laundering
Stage 1 (Transfer): Within 2 seconds, funds are moved from victim addresses before disclosure
Stage 2 (Laundering): On average, 10.6 days to reach final deposit points, using multi-layer routing to evade tracking
Trend Shift: Faster transfers (84.6% before disclosure), slower laundering (from 8 to 10.6 days)
This shift reflects increased regulation after disclosures. Once an incident is public, exchanges and blockchain analysis firms flag addresses and tighten scrutiny. Attackers respond by splitting funds into smaller amounts, using multi-layer routing, and then attempting to cash out.
Bridging $2.01 Billion and the Revival of Tornado Cash
(Source: Global Ledger)
Bridges have become the main channel in this process. Nearly half of stolen funds—about $2.01 billion—are transferred via cross-chain bridges, more than three times the amount moved through mixers or privacy protocols. In last year’s high-profile CEX hack, 94.91% of stolen funds flowed through bridging protocols.
Cross-chain bridges are favored for laundering because of their convenience and concealment. When hackers move stolen ETH through bridges to BNB Chain or Polygon, tracking becomes much harder. Different address formats across chains, separate blockchain explorers, and the need for law enforcement to coordinate across chains all buy hackers time. Additionally, many smaller chains have less mature monitoring and analysis tools than Ethereum, making it easier for stolen funds to “disappear” after transfer.
The $2.01 billion accounts for roughly 50% of the total stolen amount in 2025, which is $4.04 billion. This concentration on a single laundering channel presents both opportunities and challenges for law enforcement. Strengthening monitoring of bridges—such as requiring KYC for bridge protocols or freezing suspicious transactions—could potentially intercept half of crypto laundering activities. The challenge is that most bridges are decentralized, with no central authority to enforce such measures.
Meanwhile, Tornado Cash has regained attention. The protocol appeared in 41.57% of hacking incidents in 2025. The report notes that due to sanctions policy changes, its usage surged in the second half of the year. Tornado Cash is an Ethereum-based mixing protocol that blends multiple users’ funds, making it extremely difficult to trace the origin of specific assets. The U.S. Treasury added Tornado Cash to sanctions lists in 2022, but its smart contracts remain on-chain and cannot be shut down.
The 41.57% incidence rate shows that even under sanctions risk, hackers heavily rely on Tornado Cash. This may be due to: reduced enforcement during the Trump administration, hackers willing to take sanctions risks for privacy, or Tornado Cash’s superior technical effectiveness compared to other mixers. This “sanctions evasion” phenomenon highlights the fundamental challenge of regulating decentralized protocols.
The Strange Phenomenon of Half the Stolen Funds Remaining Dormant
At the same time, the amount of funds directly withdrawn to centralized exchanges in the second half of the year dropped sharply. The share of stolen funds in DeFi platforms increased. Attackers seem to avoid obvious withdrawal channels until attention shifts elsewhere. Notably, analysis shows about 49% of stolen crypto remains unused. This means billions of dollars are still sitting in wallets, potentially for future laundering.
This 49% of unspent funds is highly peculiar. It amounts to roughly $1.98 billion controlled by hackers but not yet moved or laundered. Possible reasons include: hackers waiting for media attention to fade before acting, the sheer volume of funds making quick laundering impractical, or long-term investors holding Bitcoin as a store of value without rushing to cash out.
This “hiding” strategy is a double-edged sword for asset recovery. On one hand, as long as funds remain untouched, there’s a chance for law enforcement to trace and recover them if they can identify the hackers and seize their keys. On the other hand, these funds could suddenly be laundered months or years later, after media interest wanes and monitoring efforts decline, increasing the likelihood of successful laundering.
The severity of the problem remains significant. Ethereum losses alone amount to $2.44 billion, representing 60.64% of total losses. There were 255 theft incidents involving a total of $4.04 billion. However, recovery remains limited: only about 9.52% of stolen funds have been frozen, and just 6.52% have been ultimately returned.
This extremely low recovery rate—only 6.52%—is one of the most frustrating realities of crypto crime. In traditional finance, recovery rates for bank robberies or wire fraud typically range from 30% to 50%, thanks to regulated institutions that can freeze and seize funds. In crypto, once funds move into hacker-controlled wallets, recovery is nearly impossible unless hackers voluntarily return or law enforcement seizes their keys. This “permanent loss upon theft” characteristic is one of the biggest security risks in crypto assets.
Overall, these findings reveal a clear pattern: attackers initiate their assault within seconds, using automated, machine-speed operations. Defenders respond slowly, forcing criminals to adopt more deliberate, complex laundering strategies. The race is ongoing, but it has shifted from a matter of seconds to days.
Related Articles
SEC crypto enforcement under attack by Congress, is U.S. digital asset regulation at a critical crossroads?
Caixin: A hearing will be held on February 16th for the case involving 60,000 Bitcoins laundering, with the amount involved exceeding 30 billion yuan and affecting nearly 130,000 Chinese victims.
U.S. banking lobbying group warns "too rapid approval": OCC crypto license approval faces significant resistance
The EU plans to fully block Russian crypto transactions, and related banks have also been included.
X Platform Million Dollar Prize Winner Exposes Scam! Bubblemaps Reveals Meme Coin Fraud Profits of $600,000